TLS Deprecation Guide
As of 2025, support for TLS 1.0 and 1.1 has been deprecated across many platforms and JVMs. FusionReactor requires a modern TLS connection to activate and communicate securely.
The TLS Probe helps you test whether your system can successfully establish a secure HTTPS connection, and it shows the encryption method (cipher suite) being used.
Running the TLS Probe
- Download the
tls-probe.jarfile here. - From a command line or terminal in the folder containing the JAR file, run:
Understanding the results
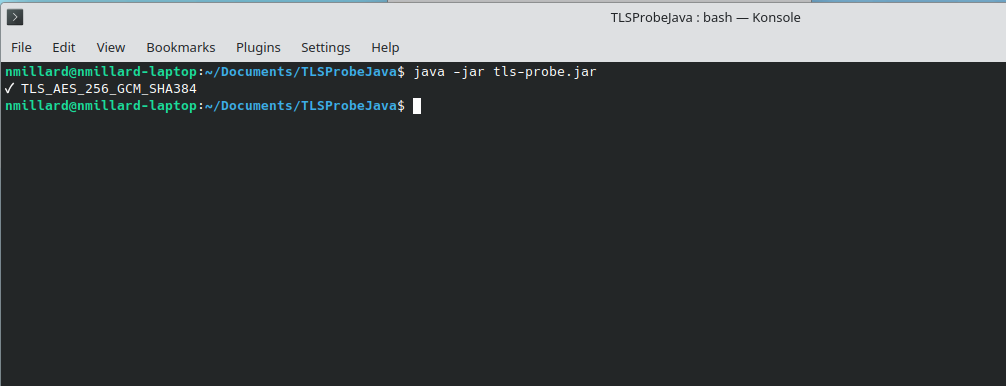
✅ Successful connection
Example output:
This means your system successfully connected over HTTPS. The text shown is the TLS cipher suite (the encryption method used for the connection).
Note
On some consoles, the checkmark (✓) may appear as a question mark (?) due to font or encoding differences. This does not affect the result.
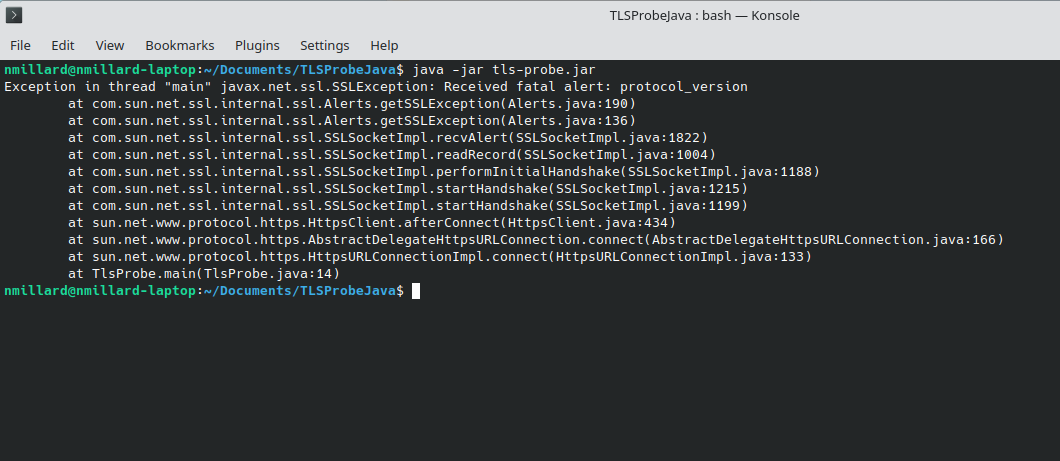
❌ Failed connection
If the connection cannot be established (e.g. unsupported TLS version, network restrictions, configuration issues), the probe will display a Java error trace instead of a cipher suite.
Example:
This means the TLS handshake failed and no secure connection was established.
Fixing TLS failures
If your system fails the TLS probe, you have three main options:
| Path | Pros | Cons | Typical Time |
|---|---|---|---|
| 1. Upgrade the JVM (recommended) | Future-proof, faster, fewer CVEs | May require application re-testing | ~30 min |
| 2. Retrofit your current JVM | No code changes | Must repeat per host; still legacy | ~10 min |
| 3. Manual / Offline activation | Works even on very old Java (5+) | No auto-renew; manual process per server | ~5 min |
Path 1 – Upgrade the JVM (Preferred)
- Install Java 8u121+, 11, 17, or 21.
- Point your service to use the new JVM.
- Restart your Application Server.
Done.
Path 2 – Retrofit your current JVM
-
Download ISRG Root X1 and X2 certificates from Let’s Encrypt.
-
Import the roots into your JVM keystore:
-
Force TLS 1.2 (for Java 7 / early 8) by adding this line to:
-
For Java 6 only, install BouncyCastle JSSE:
-
Copy
bcprovandbctlsJARs to$JAVA_HOME/lib/ext -
Add this to
java.security:
Learn more
Path 3 – Manual / Offline Activation
Use this if you cannot enable TLS 1.2 or add Let’s Encrypt roots.
Note
Not available for FusionReactor Cloud licenses due to internet connection requirements.
- In the FusionReactor On-Premise UI, go to About → Manual Activation.
- Copy the activation code.
- On an internet-connected machine, open https://fusion-reactor.com/manual.
- Paste the activation code and click Activate.
- Copy the generated activation key.
- Back in the FusionReactor UI, paste the activation key and click Activate.